- SSH KeyGen is a simple process that creates a public/private SSH Key-pair that can be used to securely access a virtual private server. Get started on Windows via PuTTY Download or jump right in on.
- .has to send their public key to you or whoever is administrating the Git server (assuming you’re using an SSH server setup that requires public keys).
- After the key pair has been generated, copy the public key from the top of. Use the key from the top of the window when entering a key in the SSH Keys.
In this step by step tutorial, we will be discussing how to configure SSH key-based authentication in Linux operating systems.
Contents
|
Parent page: Internet and Networking >> SSH
Public key authentication is more secure than password authentication. This is particularly important if the computer is visible on the internet. If you don't think it's important, try logging the login attempts you get for the next week. My computer - a perfectly ordinary desktop PC - had over 4,000 attempts to guess my password and almost 2,500 break-in attempts in the last week alone.
With public key authentication, the authenticating entity has a public key and a private key. Each key is a large number with special mathematical properties. The private key is kept on the computer you log in from, while the public key is stored on the .ssh/authorized_keys file on all the computers you want to log in to. When you log in to a computer, the SSH server uses the public key to 'lock' messages in a way that can only be 'unlocked' by your private key - this means that even the most resourceful attacker can't snoop on, or interfere with, your session. As an extra security measure, most SSH programs store the private key in a passphrase-protected format, so that if your computer is stolen or broken in to, you should have enough time to disable your old public key before they break the passphrase and start using your key. Wikipedia has a more detailed explanation of how keys work.
Public key authentication is a much better solution than passwords for most people. In fact, if you don't mind leaving a private key unprotected on your hard disk, you can even use keys to do secure automatic log-ins - as part of a network backup, for example. Different SSH programs generate public keys in different ways, but they all generate public keys in a similar format:
Key-based authentication is the most secure of several modes of authentication usable with OpenSSH, such as plain password and Kerberos tickets. Key-based authentication has several advantages over password authentication, for example the key values are significantly more difficult to brute-force, or guess than plain passwords, provided an ample key length. Other authentication methods are only used in very specific situations.
SSH can use either 'RSA' (Rivest-Shamir-Adleman) or 'DSA' ('Digital Signature Algorithm') keys. Both of these were considered state-of-the-art algorithms when SSH was invented, but DSA has come to be seen as less secure in recent years. RSA is the only recommended choice for new keys, so this guide uses 'RSA key' and 'SSH key' interchangeably.
Key-based authentication uses two keys, one 'public' key that anyone is allowed to see, and another 'private' key that only the owner is allowed to see. To securely communicate using key-based authentication, one needs to create a key pair, securely store the private key on the computer one wants to log in from, and store the public key on the computer one wants to log in to.
Using key based logins with ssh is generally considered more secure than using plain password logins. This section of the guide will explain the process of generating a set of public/private RSA keys, and using them for logging into your Ubuntu computer(s) via OpenSSH.
The first step involves creating a set of RSA keys for use in authentication.
This should be done on the client.
To create your public and private SSH keys on the command-line:
You will be prompted for a location to save the keys, and a passphrase for the keys. This passphrase will protect your private key while it's stored on the hard drive:
Your public key is now available as .ssh/id_rsa.pub in your home folder.
Congratulations! You now have a set of keys. Now it's time to make your systems allow you to login with them
Choosing a good passphrase
You need to change all your locks if your RSA key is stolen. Otherwise the thief could impersonate you wherever you authenticate with that key.
An SSH key passphrase is a secondary form of security that gives you a little time when your keys are stolen. If your RSA key has a strong passphrase, it might take your attacker a few hours to guess by brute force. That extra time should be enough to log in to any computers you have an account on, delete your old key from the .ssh/authorized_keys file, and add a new key.
Your SSH key passphrase is only used to protect your private key from thieves. It's never transmitted over the Internet, and the strength of your key has nothing to do with the strength of your passphrase.
The decision to protect your key with a passphrase involves convenience x security. Note that if you protect your key with a passphrase, then when you type the passphrase to unlock it, your local computer will generally leave the key unlocked for a time. So if you use the key multiple times without logging out of your local account in the meantime, you will probably only have to type the passphrase once.
Pre Generated Ssh Host Keys Free
If you do adopt a passphrase, pick a strong one and store it securely in a password manager. You may also write it down on a piece of paper and keep it in a secure place. If you choose not to protect the key with a passphrase, then just press the return when ssh-keygen asks.
Key Encryption Level
Note: The default is a 2048 bit key. You can increase this to 4096 bits with the -b flag (Increasing the bits makes it harder to crack the key by brute force methods).
Password Authentication
The main problem with public key authentication is that you need a secure way of getting the public key onto a computer before you can log in with it. If you will only ever use an SSH key to log in to your own computer from a few other computers (such as logging in to your PC from your laptop), you should copy your SSH keys over on a memory stick, and disable password authentication altogether. If you would like to log in from other computers from time to time (such as a friend's PC), make sure you have a strong password.
The key you need to transfer to the host is the public one. If you can log in to a computer over SSH using a password, you can transfer your RSA key by doing the following from your own computer:
Where <username> and <host> should be replaced by your username and the name of the computer you're transferring your key to.
Due to this bug, you cannot specify a port other than the standard port 22. You can work around this by issuing the command like this: ssh-copy-id '<username>@<host> -p <port_nr>'. If you are using the standard port 22, you can ignore this tip.
Another alternative is to copy the public key file to the server and concatenate it onto the authorized_keys file manually. It is wise to back that up first:
You can make sure this worked by doing:
You should be prompted for the passphrase for your key:
Enter passphrase for key '/home/<user>/.ssh/id_rsa': |
Enter your passphrase, and provided host is configured to allow key-based logins, you should then be logged in as usual.
Encrypted Home Directory
If you have an encrypted home directory, SSH cannot access your authorized_keys file because it is inside your encrypted home directory and won't be available until after you are authenticated. Therefore, SSH will default to password authentication.
To solve this, create a folder outside your home named /etc/ssh/<username> (replace '<username>' with your actual username). This directory should have 755 permissions and be owned by the user. Move the authorized_keys file into it. The authorized_keys file should have 644 permissions and be owned by the user.
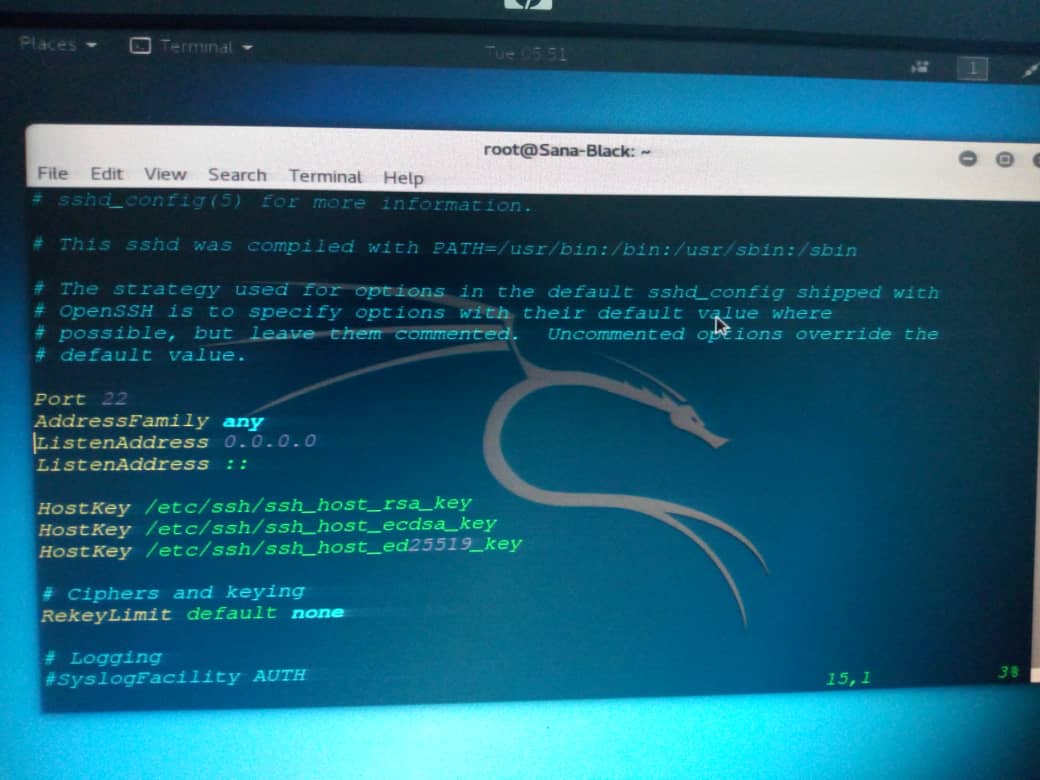
Then edit your /etc/ssh/sshd_config and add:
Finally, restart ssh with:
The next time you connect with SSH you should not have to enter your password.
username@host's password:
If you are not prompted for the passphrase, and instead get just the
prompt as usual with password logins, then read on. There are a few things which could prevent this from working as easily as demonstrated above. On default Ubuntu installs however, the above examples should work. If not, then check the following condition, as it is the most frequent cause:
On the host computer, ensure that the /etc/ssh/sshd_config contains the following lines, and that they are uncommented;
If not, add them, or uncomment them, restart OpenSSH, and try logging in again. If you get the passphrase prompt now, then congratulations, you're logging in with a key!
Permission denied (publickey)
If you're sure you've correctly configured sshd_config, copied your ID, and have your private key in the .ssh directory, and still getting this error:
Permission denied (publickey). |
Chances are, your /home/<user> or ~/.ssh/authorized_keys permissions are too open by OpenSSH standards. You can get rid of this problem by issuing the following commands:
Error: Agent admitted failure to sign using the key.
This error occurs when the ssh-agent on the client is not yet managing the key. Issue the following commands to fix:
This command should be entered after you have copied your public key to the host computer.
Debugging and sorting out further problems
The permissions of files and folders is crucial to this working. You can get debugging information from both the client and server.
if you think you have set it up correctly , yet still get asked for the password, try starting the server with debugging output to the terminal.
To connect and send information to the client terminal
No matter how your public key was generated, you can add it to your Ubuntu system by opening the file .ssh/authorized_keys in your favourite text editor and adding the key to the bottom of the file. You can also limit the SSH features that the key can use, such as disallowing port-forwarding or only allowing a specific command to be run. This is done by adding 'options' before the SSH key, on the same line in the authorized_keys file. For example, if you maintain a CVS repository, you could add a line like this:
When the user with the specified key logged in, the server would automatically run /usr/bin/cvs server, ignoring any requests from the client to run another command such as a shell. For more information, see the sshd man page. /755
Documentation
Working with SSH Keys
SSH keys are required in order to provide secure connection with the remote git host specified in the Repository Origin field which can be accessed via Connect to Git Repositoryor in Edit repository/integration settings. The Git Integration for Jira app uses one set of keys for accessing all configured repositories.
Follow this guide if you are one of the users who wre limited to or wanted to use SSH to securely connect to your git repositories.
Introduction
There are two options available for specifying SSH keys:
- SSH keys stored on server filesystem. The keys are located in the home folder of the user which account is used to run Jira. This option provides better compatibility with installation of the previous versions of the Git Integration app. This option does not support passphrases.
- SSH keys are stored in the app configuration. The keys are added using the Git Integration app configuration. This option supports passphrases.
Getting Started
Before connecting repositories via SSH, users are required to generate SSH keys for use with the remote git host (public key) and for Git Integration app in Jira (private key).
Generated SSH keys always come in pair. (Example: id_rsa.puband id_rsa)
For establishing safety connection with SSH, upload a public key to the SSH server and set the private key to the SSH client.
In this case, the SSH server is the Git server and the SSH client is the Jira server. Therefore:
- Git server — public key
- Jira server — private key (Git Integration for Jira > SSH Keys)
Note that Git Integration for Jira app SSH keys:
- must not be created using the OpenSSH format,
- must be the private key,
- must use the supported certificate format: RSA,
- must use the supported storage format: OpenSSL PEM.
For more information, see issue SSH key format is invalid.
Windows
For Windows, we recommend to use PuTTYand use PuTTYgen to generate public and private SSH keys.

- Launch PuTTYgen and refer to the above image for the rest of the steps on this section.
- Set Type of key to generate to RSA.
- Set Number of bits in a generated key to 4096.
- Click Generate.
- Follow screen instructions such as moving your mouse pointer on random locations on the blank area of the PuTTYgen dialog. Do this until the progress bar completely fills up and the SSH key pair is generated.
- Entering a Passphrase for the generated key is optional but will ensure a more secure connection.
- Save your generated public and private key to a file by clicking the respective options.
- Copy the generated key. This is the public key that you will be using on the SSH configuration page of your git host.
- For the private key, see the note below.
You can also use the git bash command line to generate SSH key pair. For detailed information, see Generate SSH via Git bash.
Read on the section Generating SSH Keysand follow specific information for the git host and platform that you use.
Linux/MacOS
On Linux and MacOS, this generates an SSH key in RSA format:
Generating SSH Keys
Beanstalk

- For MacOS, see Working with Git on MacOS
- For Windows, see Working with Git on Windows.
- For Linux, see Working with Git on Linux.
Bitbucket
- For MacOS/Linux, see Setting up SSH for Git on MacOS/Linux.
- For Windows, see Installing or Upgrading Git - Step 1then Set up SSH for Git.
Gerrit
- For information about Gerrit software, see Gerrit Software Wiki and Gerrit at Code Review.
- For general reference and installation, see Gerrit documentation. Ubuntu installation and fixing registration error.
- For information on SSH on Gerrit, see SSH and Gerrit.
- For details on User Change-Ids, see Change-Ids in Gerrit.
GitBlit
- For information about Gitblit, see GitBlit.
- For general reference and installation, see GitBlit Configuration, Using HTTP/HTTPS Transport and Built-in Authentication.
- For information on SSH on GitBlit, see GitBlit: Using the SSH Transport.
- For GitBlit related FAQ, see GitBlit Frequently Asked Questions.
GitHub
- For MacOS, see Generating SSH Keys on MacOS.
- For Windows, see Generating SSH Keys on Windows.
- For Linux, see Generating SSH Keys on Linux.
GitLab
- See reference, Installing Git for MacOS/Windows/Linux.
- For creating SSH keys, see Generating SSH Public Key. Also see the video demonstrationhere.
GitLab CE/EE
Follow the above GitLab references for GitLab CE/EE. Then verify that your GitLab server should have the following SSH settings:
Pre-generated Ssh Host Keys
- Enabled Git access protocols -- Both SSH and HTTP(s)
- RSA SSH keys -- Are allowed
Other SSH key formats may be supported by Git Integration for Jira app, but prefer to use RSA format for your SSH git connections.
Git-scm
- See reference, Installing Git for MacOS/Windows/Linux.
- For creating SSH keys, see Connecting to GitHub with SSH.
Gitolite
- For full reference and installation, see All About Gitolite.
- For information on SSH on Gitolite, see SSH and Gitolite.
- For details on user key management, see Managing User Keys in Gitolite.
Pre Generated Ssh Host Keys List
VSTS/TFS/Azure DevOps/Azure Repos
- For information about TFS/Azure DevOps Server, see MS Team Foundaton Server.
- For general reference and terms, see Git Experience Futures.
For generating SSH keys for Azure Repos (which is applicable to MS git hosts), follow instructions at Use SSH Key Authentication.
Adding a Private SSH Key (Jira Server)
- From your Jira dashboard menu, go to Git > Manage (Git) repositories. On the sidebar under Git Integration for Jira, select SSH Keys.Alternatively, go to Jira Administration > Applications. On the sidebar under Git Integration for Jira, select SSH Keys.
- Click Add SSH Key. The following screen is displayed.
Utilize the following options for adding the new SSH key:
Option Description Key name Enter a meaningful name for this private SSH key as required. Private key This is the actual private SSH key. Upload the private key file via Browse... or paste the generated private key into the provided field. Passphrase Optional. Enter the passphrase that was assigned to this private key. - Click to complate this setup.
Adding an SSH Public Key
Add a public SSH key to your remote git host to prepare its repositories for connection with the Git Integration for Jira app.
- Login to your remote git host.
- Go to the SSH configuration page, if supported.
- Paste the public key to the provided box and complete the setup.
SSH Keys Configuration (Jira Server)
Manage and associate SSH keys to connected git repositories via the SSH Keys in Git Integration for Jira Server app repository configuration page.
The list of added private SSH keys is accessible on this page. Both types of SSH keys are displayed in this list. Legacy filesystem-based keys contain directory path in the Private key column.
Refer to the following table for list column information:
| Option | Description |
|---|---|
| Name | The name of the private SSH key will appear here. |
| Private key | This is the private SSH key in hex mode. |
| Passphrase | A lock icon is displayed if the SSH key pair has a passphrase. |
| Associations | Lists the repositories that are associated with this SSH key. |
| Last used by | Lists the repositories that are using this SSH key. |
| Operations | Click the icon to perform Delete or Associations functions. |
Adding and Associating SSH Keys
Limit the usage of the SSH key by associating them to selected repositories. As of v2.6.9 of the Git Integration for Jira app, the option to strictly map keys to repositories is available.
On the SSH Keys page, click Actions > Associations for the selected SSH key.
The following screen is displayed:
Mark the required repository or repositories to associate the SSH key.
Clicking the Select All text label marks all repositories that will be associated to this SSH key.
Clicking the Select None text label deselects all repositores.
Click Save to save the settings.
Pre Generated Ssh Host Keys Download
If you have multiple repositories that uses the same SSH key, configure them via Git Integration app by doing the following steps:
- Configure a repository that requires an SSH key via Add Repository Wizard.
- Associate that SSH key with the currently configured repository via SSH Keys.
- Add another repository that requires the same SSH key. You will be presented with the following screen:
- Select the SSH key that you have associated to the previously added repository from the Existing key list.
- Click Next to continue. Complete the wizard and add another repository as desired.
For third-party products or services (such as GitHub, GitLab, Bitbucket, etc.), register the PUBLIC KEY for target repository or in profile settings of your git account.
For custom git hosting servers, ask your administrator to check that the target keypair's PUBLIC KEY is added into the authorized_keys file of the git server. For more information, see the following article.
Removing SSH Keys
SSH keys cannot be modified or updated. To change the keys, remove and add them again.

Reconfigure Git Repository and SSH Key
Perform the following steps to reconfigure repositories and SSH key:
- Remove any old SSH keys configured with the Git Integration app via <JiraHOSTNAME> /secure/ViewSshKeys.jspa
- Restart Jira.
- Get the following file from your Jira server to your Windows workstation: /home/jira/.ssh/id_rsa
- Set up the git repository in Jirausing the repository location and upload the private key that was downloaded above.
For multiple repository configuration, see Bulk change.
Connecting SSH Git Repositories (Jira Cloud)
Pre Generated Ssh Host Keys
SSH git repositories can be integrated with Jira Cloud via Git Integration for Jira app.
- Generate an SSH key pair. We recommend to generate a 4096-bit key.
- Obtain the Clone SSH git URL from your git host repository page.
- On your Jira Cloud dashboard, go to menu Git > Manage Git repositories.
- On the Auto-connect integration panel, click Git.
- Paste the clone URL into the Remote Git URL field.
- Click Next.
- Click Connect.
- Paste the Private SSH key on the provided box or click Upload Key File to upload a private SSH key file.
- Enter the Passphrase of the private SSH key, if any. Otherwise, leave it blank.
- Click Connect.
The connected repository is listed in the git configuration page.